Host certificate
Since the authentication and authorization of resources and people working in Grid-related areas, is performed by a Public Key Infrastructure (PKI), participation in Grid Computing requires a certificate that adheres to the specifications of the European Policy Management Authority for Grid Authentication in e-Science (EUGridPMA). Due to the cooperation of the EUGridPMA and the corresponding american (TAGPMA) and Asia-Pacific (APGridPMA) associations, these certificates have a worldwide scope within the scientific field.
For Germany, members of the EUGridPMA are the DFN - German Research Network and the Karlsruhe Research center(FZK). The aforementioned organisations operate a so called Certification Authority (CA), which is commissioned to generate Certifications adhering to the EUGridPMA specifications. In order for an electronic certificate to be identified with one person or resource, it is necessary that the owner or the party responsible for the resource, respectively, appear personally to one of these CAs along with an appropriate document to verify his identity.
To simplify this process for the users, the so called Registration Authorities (RA) were established. Their function is to undertake this operation on behalf of the CA. LRZ is authorized to operate a DFN-PKI related RA, responsible for LRZ itself and for the three Universities in Munich.
Generating a host certificate request
There are several ways to generate a host certification request. Here we will cover a middleware-agnostic way by means of OpenSSL. It is also possible to use Globus toolkit's command if you have Globus available. See Globus user guide for more information if you prefer that.
Using OpenSSL
In case OpenSSL is missing on your system you can get it from the OpenSSL website.
Configuration files
The files below contain openssl configuration information needed to generate a DFN-GridCA request for those institutions for which the LRZ-RA is responsible. Please download the file that corresponds to your institution.
- For LRZ employees or servers
- For Ludwig-Maximilians-University members or servers
- For Technical University members or servers
- For Universität der Bundeswehr members or servers
Certificate request generation
You should open a terminal and type in the following command:
openssl req -config <lrz|lmu|tum|ubw>_openssl.cnf -new -nodes -keyout hostkey.pem > hostcert_request.pem
If you already have a password-less private key you can use this key using the following command:
openssl req -config <lrz|lmu|tum|ubw>_openssl.cnf -new -key <PrivateKey>.pem > hostcert_request.pem
After the command is executed, you will be asked to answer a few questions:
Country Name (2 letter code) [DE]: [Return] (Uses the default setting)
Organization Name (eg, company) [GridGermany]: [Return]
Organizational Unit Name (eg, section) [<Name der Institution>]: [Return]
Common Name []: <Name der Ressource (full qualified hostname)>
(In a unix system you can find this by typing: hostname -f.)
Email Address []: <Email address of the person responsible for the resource>
Two files are going to be generated with this process. The file hostkey.pem contains the private key and the file hostcert_request.pem, the certificate request that should be signed by a certificate authority.
Sending your certificate request
In order to send your certificate request to the LRZ RA you should go to the following webpage. There, clicking on the "Serverzertifikat" will take you to a page looking like this:
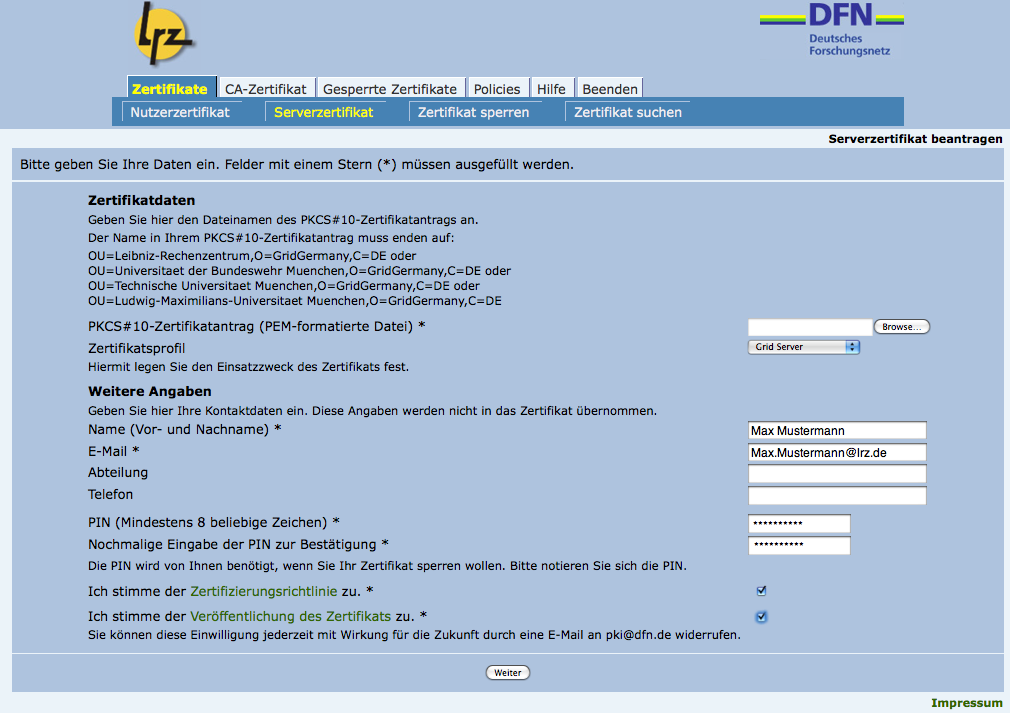
After filling in the form you should press the button "Weiter" and another page will come forth presenting the information received for you to verify. If you would like to correct something click on the button "Ändern", otherwise click on "Bestätigen" to continue.
On the following page, click on the button "Zertifikatantrag anzeigen" for a pdf file containing the certificate request which you should present to the CA. You should send an e-mail to grid-ra@lrz.de to arrange an appointment. You should have a valid identification document with you.
A short while after the meeting you will receive an e-mail from grid-ra@lrz.de containing the certificate in text form within the message and some information for it. You should save the certificate information in a file hostcert.pem in the same directory where the file hostkey.pem is also saved.
After receiving your certificate
Check using the command
openssl x509 -in cert.pem -text,
whether the DN in the subject is correct.
Confirm the receipt of the certificate by an e-mail reply after you have verified the DFN-CA checksum (SHA1 fingerprint) using
openssl x509 -noout -fingerprint -sha1 -in cert.pem
You can now use your certificate for authentication within the grid.
For UNICORE or to import your certificate into a Web-Browser, you need to generate a so called PKCS12-keystore from the private certificates. This can be done using the following command:
openssl pkcs12 -export -in hostcert.pem -inkey hostkey.pem -name "<Ihr Name>" -out keystore.p12
Or in case you need to perform the opposite action:
openssl pkcs12 -in keystore.p12 -out output.pem
You should make sure that the certificates reside in the correct place. For Globus this should be the folder $HOME/.globus/
Some grid resource providers require (apart from the certificates) the certificate of the CA. You can either find it in the e-mail you received or download it from here:
Root certificate of the DFN-PKI Grid hierarchy (DFN-Verein PCA Grid - G01)
